Zango Adware - Insecure Auto-Update and File execution
Ref : TZO-042006-Zango
I. Backround
http://www.zangocash.com
"ZangoCash (formerly LOUDcash) is recognized
around the world as one of the best pay-per-install affiliate programs on
the Internet. ZangoCash is a subsidiary of 180solutions which
also includes Zango and MetricsDirect .
Every day, 7,500-10,000 ZangoCash affiliates distribute our software to users
who are then connected with more than 6,000 MetricsDirect advertisers."
II. Description
After the acknowledgement of an License Agreement, during Startup, the bundled
EXE contacts several servers and downloads the required Adware components.
The downloaded components are not checked for integrity
or authenticity and are executed as soon as they are downloaded.
The Following procedures are exploitable :
- Initial Install
- Auto-Update function
The condition is exploitable in the following scenarios :
- You have legitimate control over the DNS server
- You have compromised a DNS server
- You forge a cache poisoning attack against a vulnerable DNS server
- You have access to the machine and change the HOST file
.Redirecting the hostname "static.zangocash.com" to
an IP address under your Control and creating the respective V-host allows
you to install any type of executable on the machine where zango is being installed
or currently is installed, in other words: You could potentially
compromise an internal network of a company if Zango is installed on workstations
(or servers - i've seen that) and one of the 4 aforementioned conditions are
met.
Why is this an Issue ?
Especially the auto update function is a problem, imagine a DNS server (not
a split setup) is compromised or cache-poisened, every workstation with zango
installed inside the company can be immediately compromised as the Workstation
tries to automaticaly download an update of Zango and fails to realise that
instead of Zango it downloads and executes a Rootkit/Backdoor/"put anything
here".
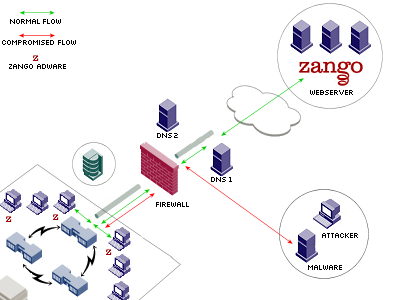
Real-life Scenario (Dns Cache Poisening, compromise etc.)
Why alter the zango address and not update.microsoft.com ?
1 - The address of the micrososoft update servers is now hardcoded
in the Operation System itself
2 - Microsoft signs and authenticates the files it downloads, it won't execute
the files if it has been messed with or is not the original file. This has
become the standard procedure in all auto-update functions I know of, several
AV vendors do the same.
Threat ?
- The Auto update problem with Zango Adware remains, there
was no fix.
- The Adware component is distributed by over 10.000 affilates
everyday and I expect it to be installed on millions of workstations
(IMO).
- If you compromise (or alter) a DNS server this gives immediate access to
internal client machines.
Mitigation ?
- Block access to static.zangocash.com or zangocash.com
althogether at the firewall.
III. Proof of Concept
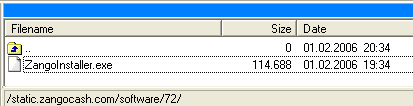
Proof of Concept Setup (Initial Install scenario)
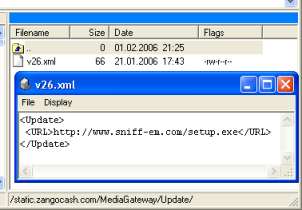
Proof of Concept Setup (Update Scenario)
The Initial Install scenario allows the execution of files deployed on the
same server. The update function seems to be used randomly querying the server
for an existing XML file, if the file exists the file is downloaded,
parsed, and the file referenced therein will be downloaded and executed.
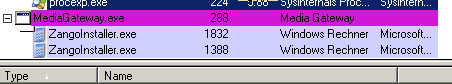
Multiple execution of the downloaded ZangoInstaller.exe (calc.exe)
IV. Summary
Vendor contact : 01/02/2006
Vendor Response : 05/02/2006
Vendor Response :
No official statement, I was not given permission to disclose the email conversations
that took place.
V. Download
Wait, what's this?
 This
is my Personal "Blog", well kind of, my name is Thierry Zoller I
am currently working as a Security Engineer and Penetration Tester for "some
company" in Luxembourg.
This
is my Personal "Blog", well kind of, my name is Thierry Zoller I
am currently working as a Security Engineer and Penetration Tester for "some
company" in Luxembourg.
On these pages i'll treat everything I enjoy and I get in touch with. This
may not be strictly related to security but may also touch parts of my personal
life.
Speaking of which, on the left that's me, I am 26 and have been involved in
the security field since I was 16. I do sports, Fitness and Body Building,
I hack various things such as cars, electronics...
Disclaimer
The views and opinion expressed herein are my personal views and are not intended to reflect the views of my employer or any other entity.