Microsoft monitors Search queries - SP2
Windows XP SP2 SearchUrl hijack lock
Issue #1 - Microsoft may monitor every search from within Internet Explorer location bar.
Issue #2 - Protection against search url modification can be circumvented.
History (Insiders
may skip)
Microsoft™ seems to have implented
a new sort of protection against the "Browser
Search Hijackers" a
common practice amongst Spyware creators. Microsoft™ introduced a convenience
feature in Internet Explorer which consist in the user simply entering a search
term like "Widgets" into the URL location bar, once he presses enter
Internet Explorer will try to resolve this address by DNS request and if it
fails it will forward the search term to their MSN™ search engine which
displays the search results for the term "Widgets" in the Browser.
Then paid search engine placement appeared and some search engine companies
in need for visitors used the affiliate scheme to bring visitors to their individual
sites. Now some aggressive affiliates tried changing the SearchURL location
which Internet Explorer™ uses to search for keywords entered in the url
location bar mentioned above. To do so they simply replaced a string in the
registry and from there on they earn a small amount of money every time you
search through the location bar and click on a result.
Details
This situation changed with Windows™ XP SP2, Microsoft™ has
locked down the SearchURL modifications, they have done so by adding a PROVIDER
key which identifies the Search engine provider. The Registry path where
the key is saved is : \Software\Microsoft\Internet Explorer\SearchUrl
For instance the provider identification
for Google™ is "gogl"
![]()
The provider keys I found by bruteforcing the provider parameter are: (gogl - Google, lyco - Lycos, yaho - Yahoo). There should be more but I stopped here rather then brute forcing through all characters.
When entering a search term in the URL location bar of Windows™ XP SP2 like "Widgets", Internet Explorer™ will first try to resolve the address "Widgets" and if it fails (it usually does except that there is a DNS entry for "Widget") it will forward the search term to MSN™ search with a parameter called "provider" and a parameter containing the search term itself. In case of "gogl", MSN™ search looks up the provider ID inside their allowed provider database and then redirects the HTTP call according to the destination URL saved in their database.
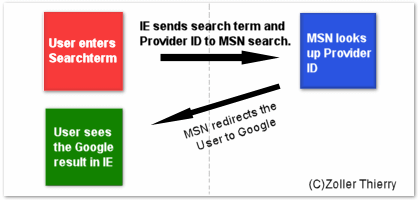
Functional scheme
| GET /response.asp?MT=SEARCHTERM&srch=3&prov=gogl&utf8
HTTP/1.1 Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: auto.search.msn.com Connection: Keep-Alive Cookie: MC1=V=3&GUID=xxxxxxxxxxxxxxxxxxxxxxxxx; smc_vid=xxxxxxxx; HTTP/1.1 302 Moved Temporarily <html><head><title>Object moved</title></head><body> |
|
Issue #1 - Microsoft
may monitor every search from within Internet Explorer™ location bar.
It is practically and theoretically possible for Microsoft™ to
monitor and data mine search terms even when those are searched over Google
or other Search engines if these search terms were
entered in the url location bar. This is possible because the MSN server which
redirects to google or to any other search engine knows about the search terms.
Issue #2 - Protection
against search url modification can be circumvented.
Since microsoft owns this virtual DNS server for Providers
ID's, it should be impossible for Browser Search Hijackers to modify the URL
since they do not have access to the MSN search database of providers and can't
modify the URL by simply manipulating the registry. However Spyware, Adware
or their affiliates can practically overcome this limitation by adding an singly
entry to the HOST
file of the targeted computer. You can find the Hosts file in \systemroot \System32\Drivers\Etc.
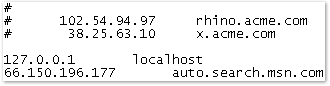
A malicious example of a DNS entry in the HOST file.
In this case, Internet Explorer will instead of
transmitting the data to auto.search.msn.com, transmit the data to the IP 66.150.196.177,
the data is send to an ASP page in the form of "/response.asp?MT=test&srch=3&prov=gogl".
We can now receive the data, either by writing an ASP script on our server
and give it the name of response.asp or use Apache mod_rewrite to rewrite the
URL to use a perl script. Either way we now have the data which we can forward
to a pay-for-performance search engine using an Affiliate ID or choose to do
otherwise.
Disclaimer
The views and opinion expressed herein are my personal views and are not intended to reflect the views of my employer or any other entity.